Turkey Hijacking IP addresses for popular Global DNS providers
At BGPmon we see numerous BGP hijacks every single day, some are interesting because of the size and scale of the hijack or as we’ve seen today because of the targeted hijacked prefixes.
It all started last weekend when the Turkish president ordered the censorship of twitter.com. This started with a block of twitter by returning false twitter IP addresses by Turk Telekom DNS servers. Soon users in Turkey discovered that changing DNS providers to Google DNS or OpenDNS was a good method of bypassing the censorship.
But as of around 9am UTC today (Saturday March 29) this changed when Turk Telekom started to hijack the IP address for popular free and open DNS providers such as Google’s 8.8.8.8, OpenDNS’ 208.67.222.222 and Level3’s 4.2.2.2.
BGP hijack
Using the Turk Telekom looking glass we can see that AS9121 (Turk Telekom) has specific /32 routes for these IP addresses. Since this is the most specific route possible for an IPv4 address, this route will always be selected and the result is that traffic for this IP address is sent to this new bogus route.
Intercepting traffic
Turk Telekom went one step further, instead of null routing this IP address they brought up servers with the IP addresses of the hijacked DNS servers and are now pretending to be these DNS servers. These new fake servers are receiving traffic for 8.8.8.8 and other popular DNS providers and are answering DNS queries for the incoming DNS requests. One of the possible reasons for impersonating these DNS providers instead of just null routing traffic to these DNS providers is that they did not want to break Internet connectivity for the significant number of Turkish users that are using these popular DNS servers.
Youtube
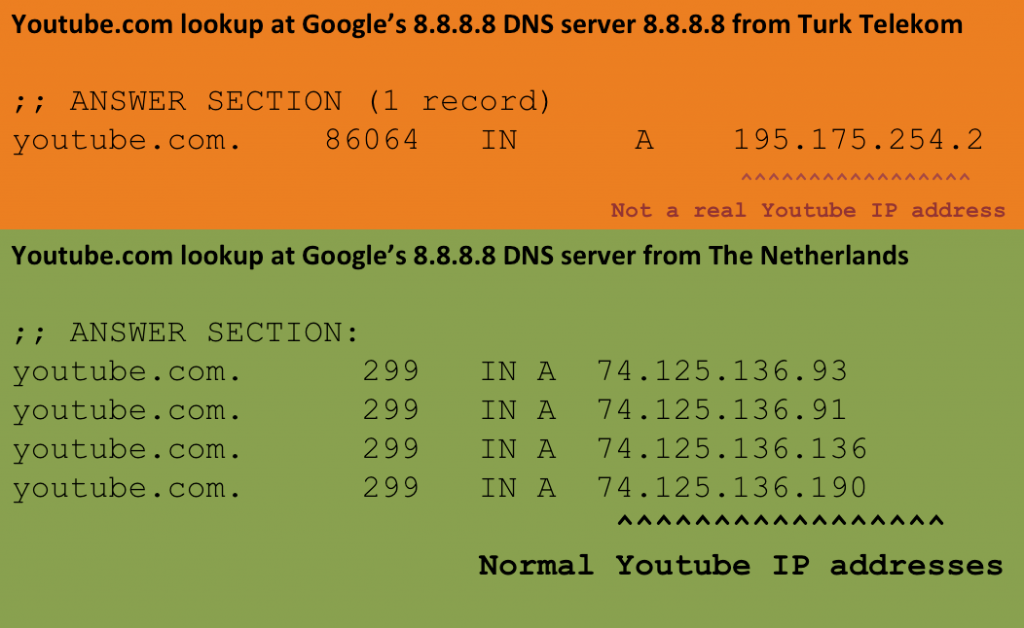
It’s likely that Turk Telekom decided to hijack these DNS servers in an effort to block access to youtube which has been ordered to be blocked as of earlier this week. Since they now receive all queries sent to free and open DNS servers they can implement the censorship on the DNS levels and now with the hijack even on DNS servers they normally do not control. The example below shows an example DNS lookup for youtube.com at 8.8.8.8 from a machine in Turk Telekom.
The output above shows that IP address returned by the ‘fake’ Google DNS server on 8.8.8.8 is 195.175.254.2. This IP is a machine on Turk Telekom and not a real Youtube server. Interestingly the returned IP is the same IP address where we've seen Twitter.com traffic for users in Turkey redirected to since last week.
Censorship
The current situation is concerning and we don’t see this type of hijacking for DNS network very much, the only note worthy exception is China where we’ve observed this several times before. Not only is Turk Telekom hijacking the IP addresses of popular DNS servers, intercepting traffic, censoring websites at will, it also has easy access to all queries being sent to these servers which allows for easy logging and recording without users noticing.

26 comments
I see examples which look like dig output with a legend “DNS lookup at 8.8.8.8 using RIPE Atlas” I’m interested in the script you used to turn Atlas’ JSON into this format 🙂
Hi Stephane,
top get the dig output I used this perl code:
https://atlas.ripe.net/docs/code/#decoding_dns_abuf
#!/usr/bin/perl
use MIME::Base64;
use Net::DNS;
use Net::DNS::Packet;
#use strict;
my $bb64 = $ARGV[0];
my $data = decode_base64($bb64);
my $packet = Net::DNS::Packet->new(\$data, 1);
The technique used in China is very different: the network elements themselves perform DPI and generate a lie when the queried name is censored (you can see that even DNS queries to non-existing IP addresses elicit an answer). As a result, no DNS server is safe.
Here, it is “simply” injection of lying routes. You can still use from Turkey open DNS resolvers, most of them are no covered by the hijacking.
Stephane,
China has some very advanced technologies to implement censorship. They use different ways of censoring DNS queries. DPI is one, BGP hijack like we see here is another one.
What is the big deal? Time warner has been doing this in S Cali, and other areas for years and no one who complains ever gets heard.
Hi Steven,
Hijacking the IP addresses of popular DNS providers and masquerade as these servers is new. It’s not simply rewriting the DNS requests, it’s hijacking IP addresses.
Obviously we’re very interested if you believe your ISP does the same, if so mail us at info at bgpmon and we’ll be happy to take a closer look.
[…] SearchTurkey Hijacking IP addresses for popular Global DNS providers […]
[…] published an interesting analysis of what is happening in the country where the Turkish Government is hijacking IP addresses for […]
[…] published an interesting analysis of what is happening in the country where the Turkish Government is hijacking IPSkype Beta […]
[…] http://www.bgpmon.net/turkey-hijacking-ip-addresses-for-popular-global-dns-providers/ […]
I am curious, if the users type in the ip address in their browser can they acces the site?
Wouldn’t it be more efficient to just drop packets to the site’s ip addresses? Why hijack DNS queries when they are so easily bypassable?
This workaround is often mentioned, by people who never tried it: 1) most Web sites are on a shared IP address and depend on the HTTP Host: header to be found 2) Even if you manage to reach the home page, the CSS and Javascript won’t load, the first click to another page will fail, etc.
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the […]
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
[…] March 29, Turk Telekom (The Turkish state-owned telecommunications company) started to hijack the IP addresses of popular free, open DNS providers, such as the Google 8.8.8.8, the OpenDNS […]
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
A bit misleading, this one. Turkey’s not actually hijacking anything (unlike what Pakistan had (allegedly unintentional) done for Youtube. What TT’s doing is having a specific route that only affects those who are using TT as the uplink for these destinations. Since TT’s not advertising these /32 prefixes to any of their upstream providers (i.e. people outside Turkey), this should/can not be called hijacking.
Even if they were advertising the /32’s, any BGP speaker accepting announces more specific than a /24 over eBGP deserves whatever wall they hit as far as I’m concerned.
That said, what TT has also done was setting up a dummy server that actually responded to DNS queries initiated for 8.8.8.8 8.8.4.4, most likely (speculating here) to get rid of support calls from people who had those statically configured in their devices, in an attempt to bypass government’s Twitter ban.
It *is* hijacking since it is not a TT prefix. Even if it is done without BGP, only in the internal routing system.
Hi, I’m Orhan, and the hijacking is still working. 8.8.8.8 Tracert ends at Ulus Ankara, where Turk Telekom and BTK(foundation that decides to whether censor or not)… And also, while pinging 8.8.8.8 it returns maximum of 15ms, but however, google.com returns a minimum of 45 ms… I guess it is still enough.
[…] latest action was “concerning” said Andree Toonk, an internet engineer at BGPMon in a blogpost, adding that it only usually saw this type of censorship in countries such as China. Via the hijack, […]
[…] over on the BGPMon blog, Andree Toonk detailed the specifics of the BGP route hijack that took place. Essentially, the Turkish ISPs started “advertising” a more specific route for […]